Just like its predecessor, Windows 11's factory default settings set by a new installation are not secure by default. Here are some steps to safeguard your privacy and data from the big tech's data mining due to improper settings, and from attackers due to misconfigured permissions.
Steps
There are quite many steps, but follow closely.
These steps have been performed on Windows 11 22H2, build 22621.525. It should be very similar on other Windows 11 versions.
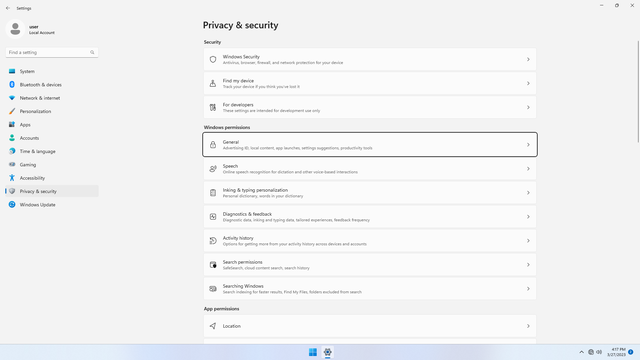
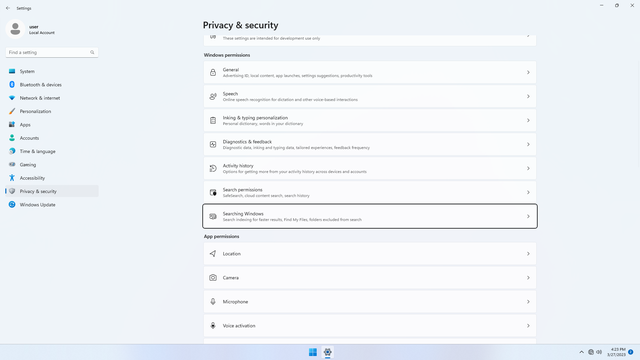
Windows permissions
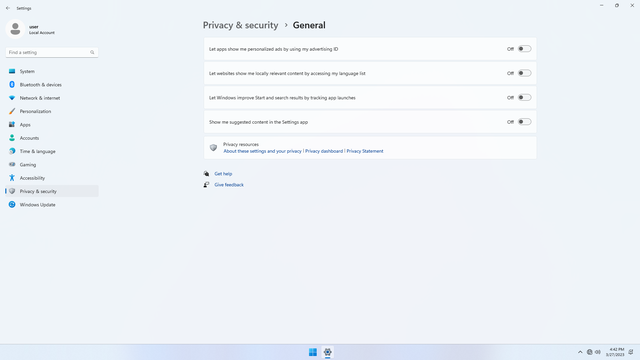
Windows permissions > General
In Settings > Privacy & security > Windows permissions > General, flip all switches off.
This is one of the most important steps to prevent Bing from following you around.
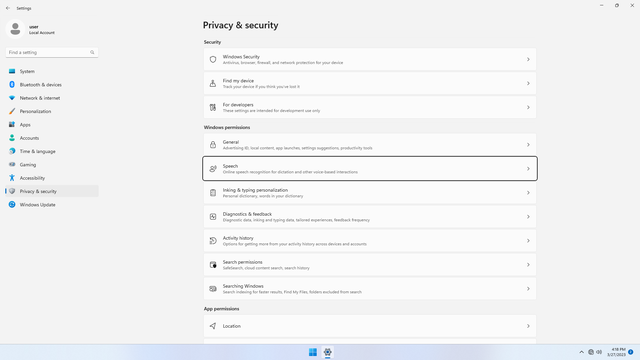
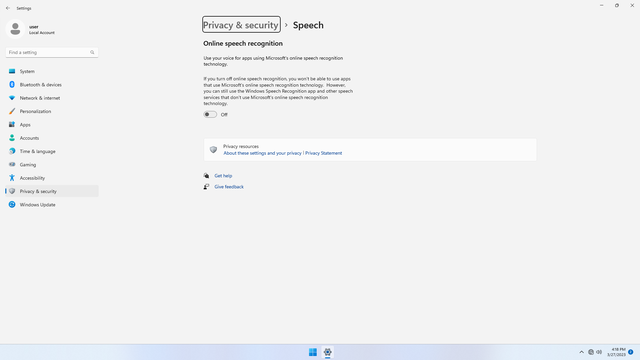
Windows permissions > Speech
In Settings > Privacy & security > Windows permissions > Speech, flip all switches off. This prevents your voice data from being sent to Microsoft.
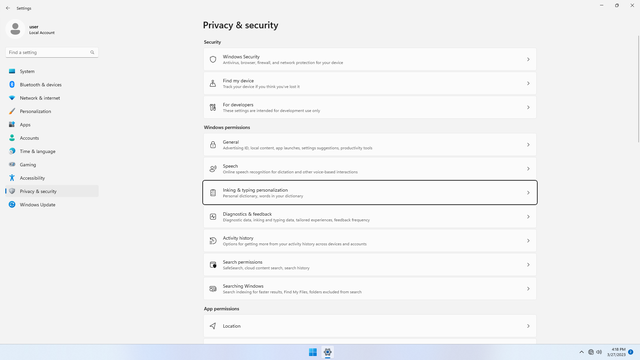
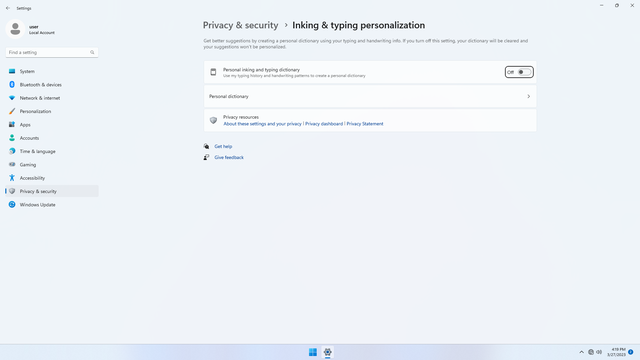
Windows permissions > Inking & typing personalization
In Settings > Privacy & security > Windows permissions > Inking & typing personalization, flip all switches off. This setting allows Cortana to learn from your typing and writing (it's really just tracking everything you type), and Cortana may suggest things to you while you type or write. It's would be sending whatever it has learnt from you back to Microsoft, so you know how much of your personal data you are giving away.
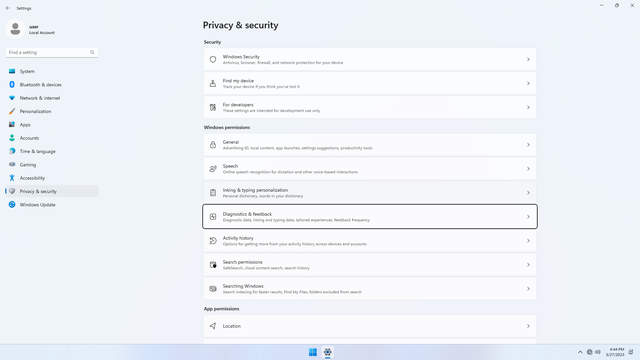
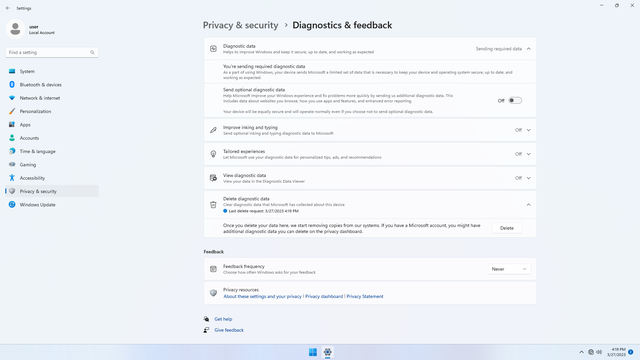
Windows permissions > Diagnostics & feedback
In Settings > Privacy & security > Windows permissions > Diagnostics & feedback, flip all switches off. This prevents unneeded diagnostics from being sent back to Microsoft, and annoying feedback popups that happen from time to time.
Click Delete diagnostic data, and click Delete to delete existing data.
Under Feedback > Feedback frequency, change to Never.
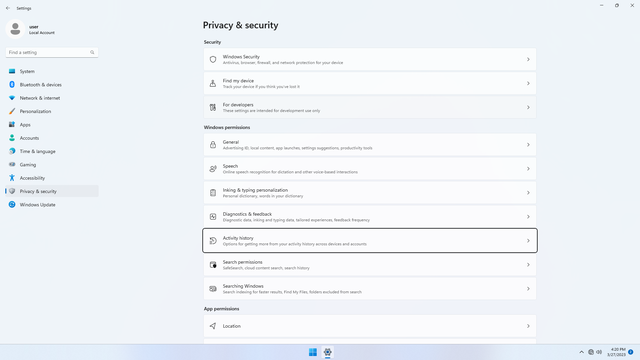
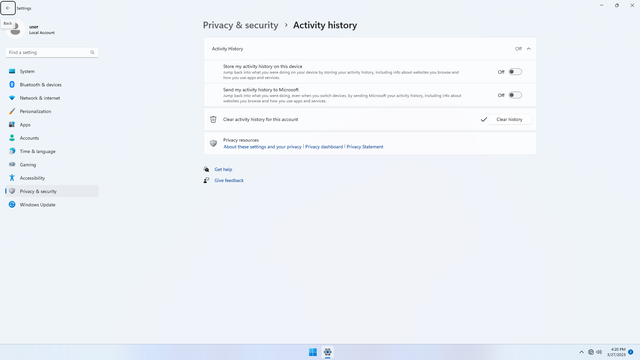
Windows permissions > Activity history
In Settings > Privacy & security > Windows permissions > Activity history, flip all switches off.
Click Clear history.
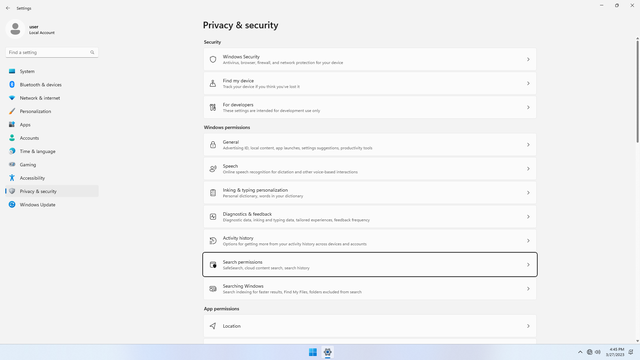
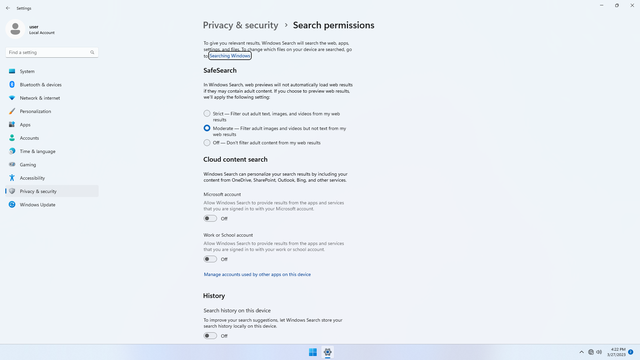
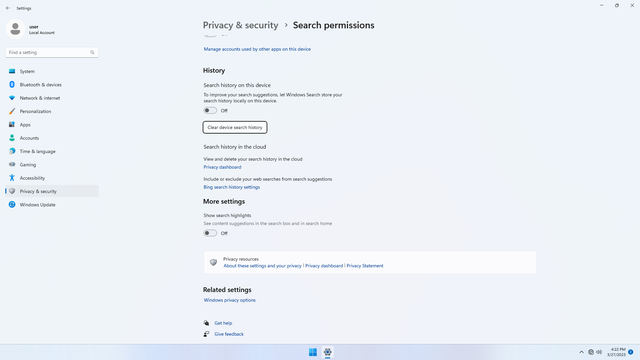
Windows permissions > Search permissions
In Settings > Privacy & security > Windows permissions > Search permissions, flip all switches off.
Under History, click Clear device search history.
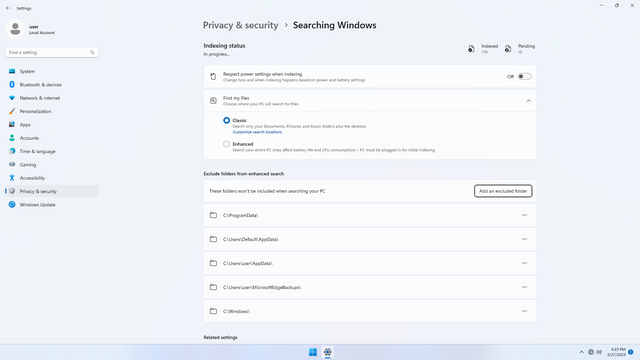
Windows permissions > Searching Windows (optional)
In Settings > Privacy & security > Windows permissions > Searching Windows, you may like to exclude certain sensitive folders from enhanced search.
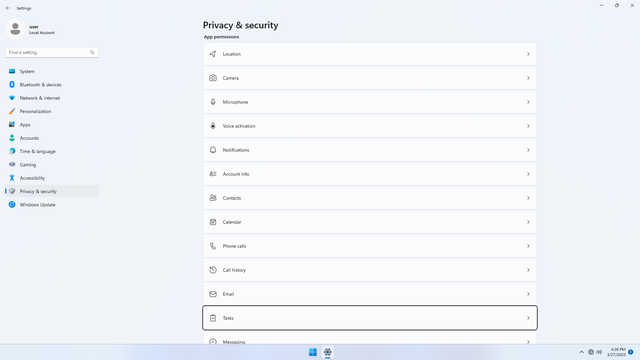
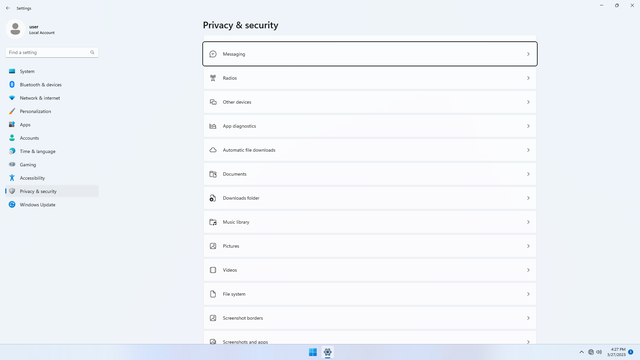
App permissions
Changing App permissions settings do not affect Win32 desktop apps, but only apps from the Microsoft Store (i.e. Metro, or Universal apps). It is best to start by toggling everything off, and then selectively granting permissions to an app only when the app requests permissions. This will give you a sense of what apps you really use, and what data they have access to on your device. It may seem tedious but it is worthwhile. If you think certain apps are old and unused, do not hesitate to delete them, since old apps might have security issues.
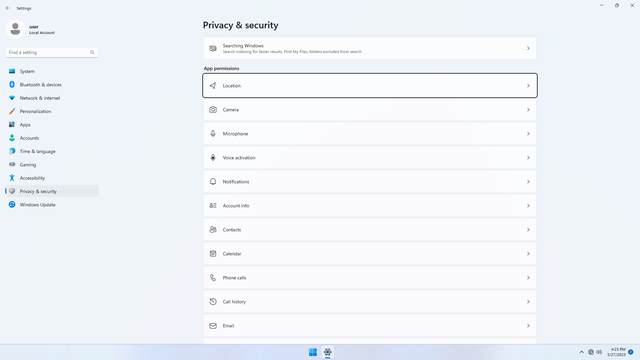
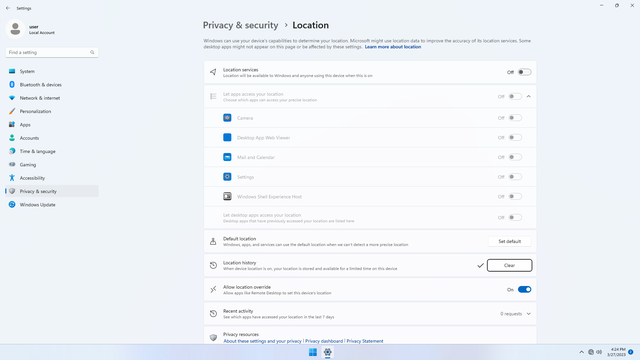
App permissions > Location
In Settings > Privacy & security > App permissions > Location, flip all switches off. Flip on only for apps you think you will use. Location may be used by malicious apps to spy on users.
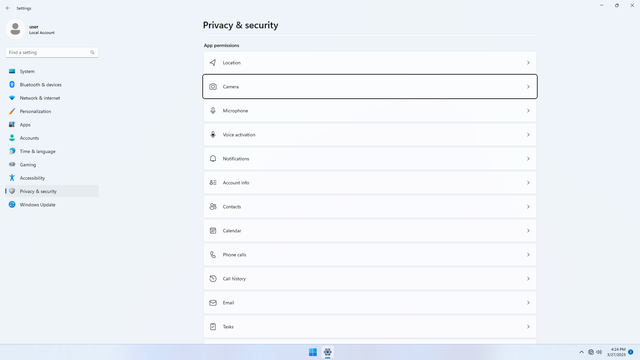
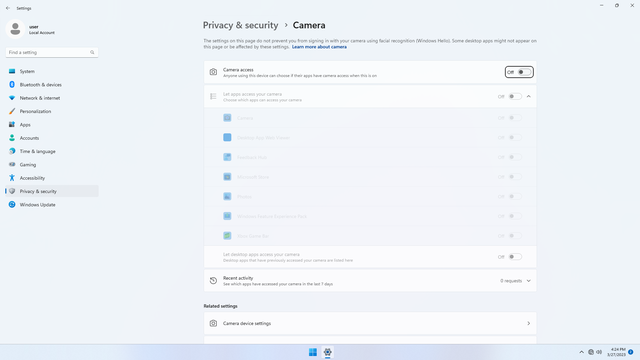
App permissions > Camera
In Settings > Privacy & security > App permissions > Camera, flip all switches off. Flip on only for apps you think you will use. Camera may be used by malicious apps to spy on users.
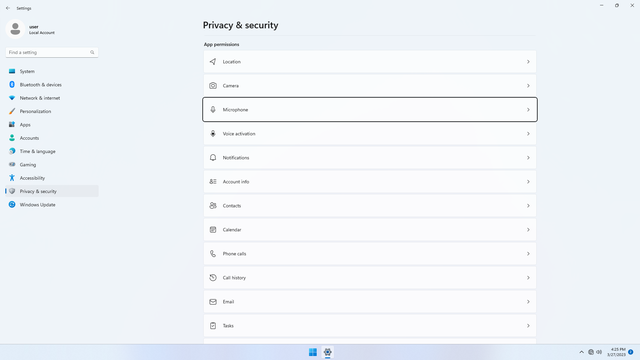
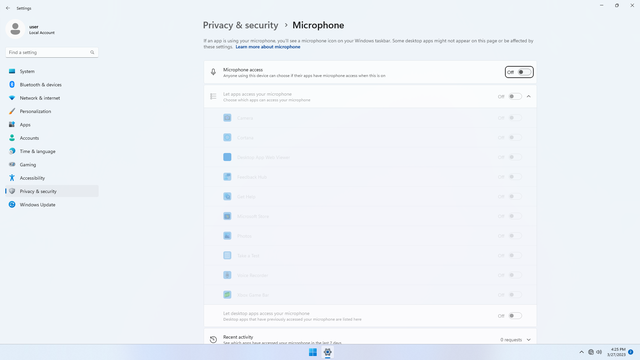
App permissions > Microphone
In Settings > Privacy & security > App permissions > Microphone, flip all switches off. Flip on only for apps you think you will use. Microphone may be used by malicious apps to spy on users.
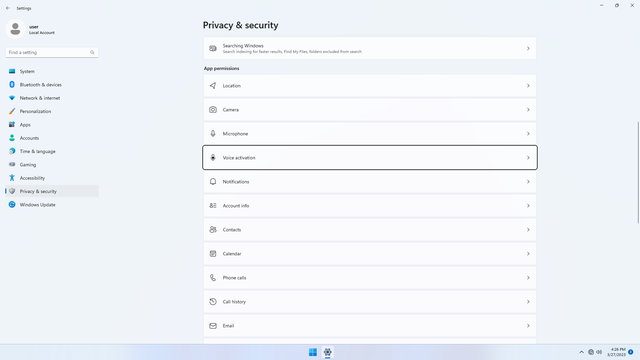
App permissions > Voice activation
In Settings > Privacy & security > App permissions > Voice activation, flip all switches off. This actually allows the app to listen for your voice perpetually, which is rather unnecessary. This does not just affect your privacy, but privacy of everyone within your device's vicinity. It is rare to need this unless it is for accessibility purposes, such as triggering an action without having the phone at hand (e.g. taking photos). It is best to keep this switch off.
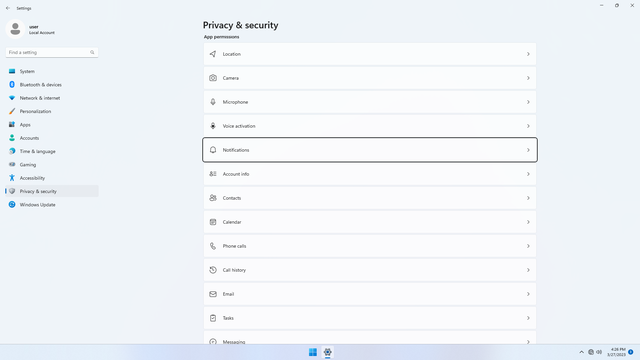
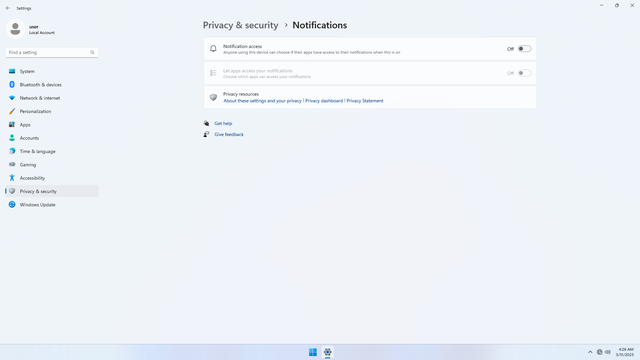
App permissions > Notifications
In Settings > Privacy & security > App permissions > Notifications, flip all switches off. Flip on only for apps you think you will use. This section basically allows apps to read all push notifications on the device, which may be useful for event-based triggering of a task, or auto-fill (e.g. auto-filling of a OTP from the Messages app when an SMS notification comes in). But it may also be a way to steal data through push notifications, e.g. OTP or password resets through email or SMS. If uncertain, turn it off and enter OTP manually instead.
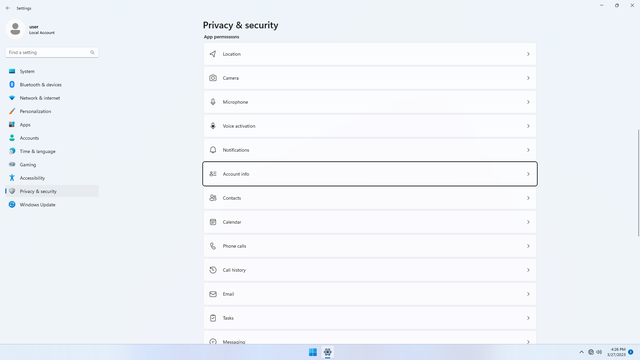
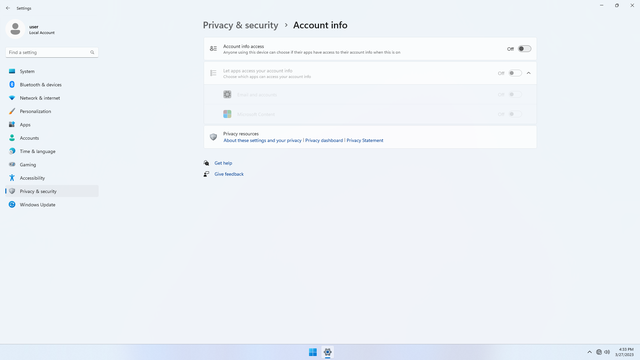
App permissions > Account info
In Settings > Privacy & security > App permissions > Account info, flip all switches off. This basically allows any app to access your personal info (e.g. your Microsoft Account basic info like your name and email, or a local user account's name and username), in case they want to use it for sign up purposes. However, to have this left on is not good, because any app may be able to request for this permission, and one may accidentally grant permissions to the app.
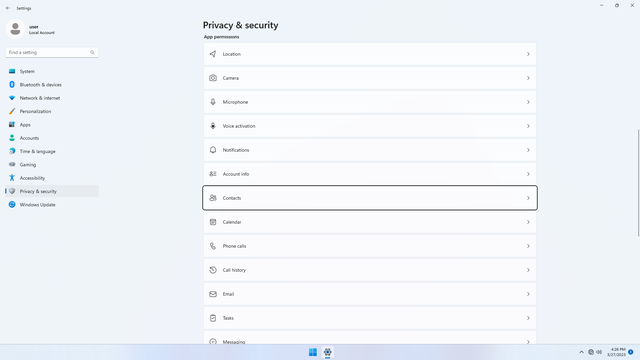
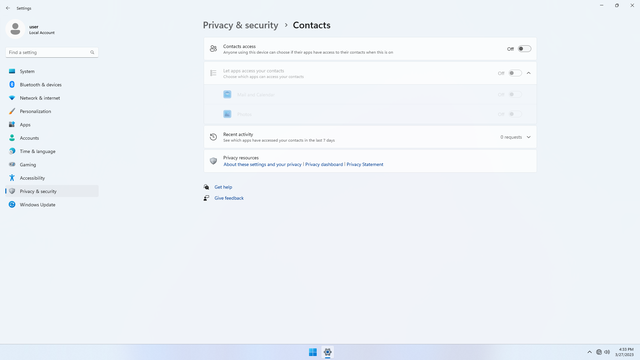
App permissions > Contacts
In Settings > Privacy & security > App permissions > Contacts, flip all switches off. Flip on only for apps you think you will use. Contacts falling into malicious hands affects not just you, but all your contacts! And tell your friends to do the same.
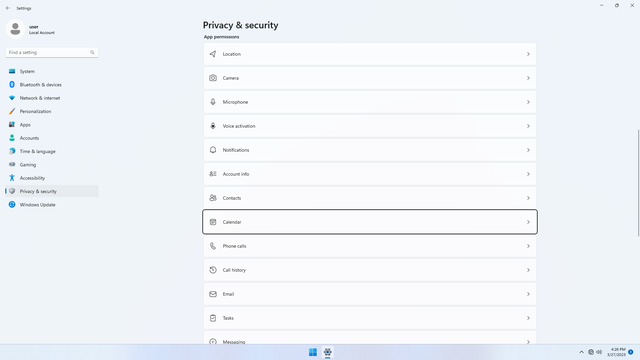
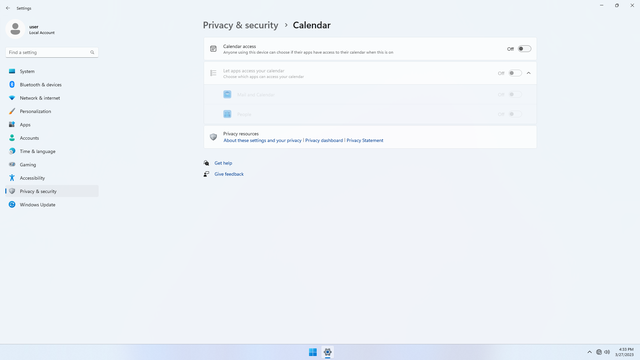
App permissions > Calendar
In Settings > Privacy & security > App permissions > Calendar, flip all switches off. Flip on only for apps you think you will use. Calendar may be used by malicious apps to spy on users.
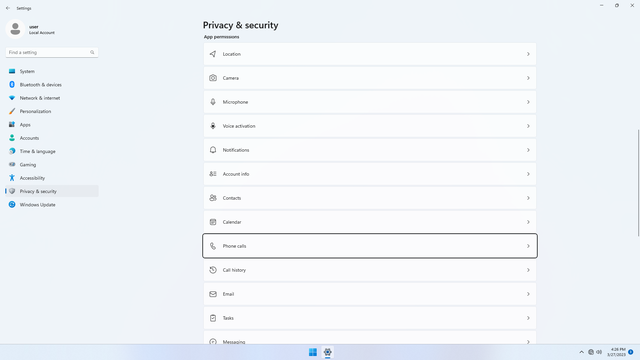
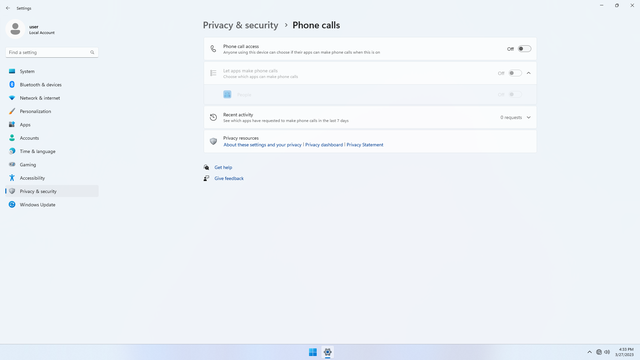
App permissions > Phone calls
In Settings > Privacy & security > App permissions > Phone calls, flip all switches off. Flip on only for apps you think you will use. Phone calls may be used by malicious apps to spy on users.
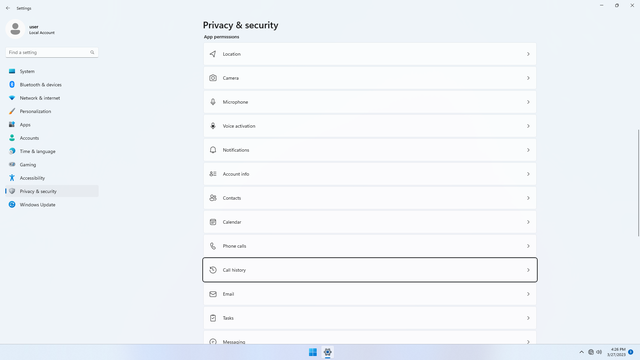
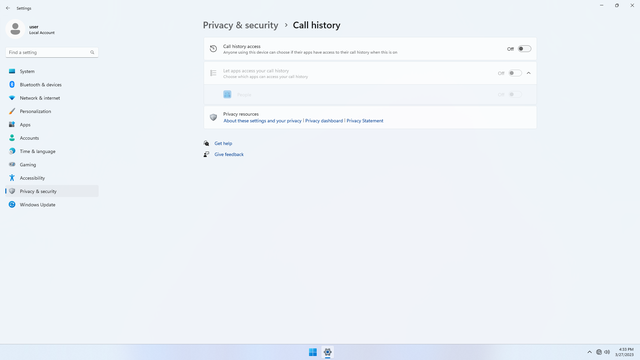
App permissions > Call history
In Settings > Privacy & security > App permissions > Call history, flip all switches off. Flip on only for apps you think you will use. Call history may be used by malicious apps to spy on users.
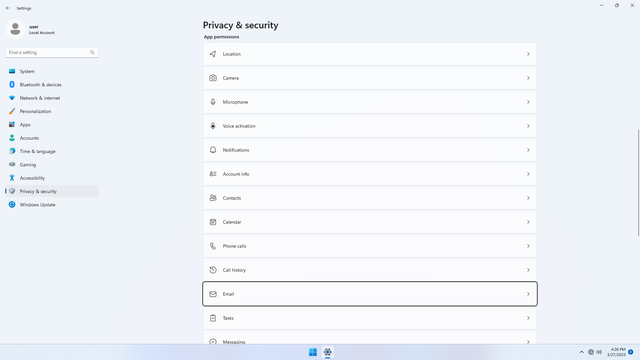
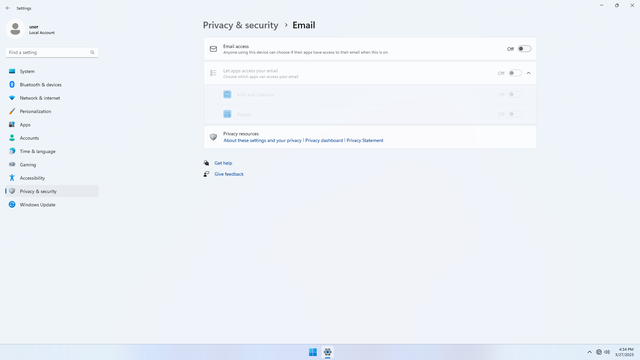
App permissions > Email
In Settings > Privacy & security > App permissions > Email, flip all switches off. Flip on only for apps you think you will use. Email falling into malicious hands can be used to get into all your other accounts by requesting a password change and impersonating you, and can result in personal data theft. Be very certain which apps should be allowed.
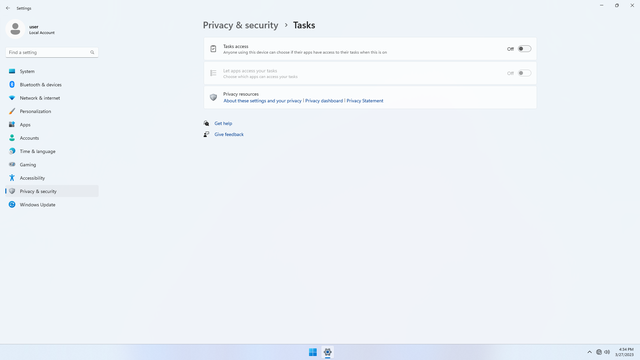
App permissions > Tasks
In Settings > Privacy & security > App permissions > Tasks, flip all switches off. Flip on only for apps you think you will use.
App permissions > Messaging
In Settings > Privacy & security > App permissions > Messaging, flip all switches off. Flip on only for apps you think you will use. Like Contacts and Email, Messaging falling into malicious hands can be used to hack into all your accounts by taking your OTP or other personal details and authenticating as you! Be very certain which apps should be allowed.
App permissions > Radios
In Settings > Privacy & security > App permissions > Radios, flip all switches off. This basically allows apps to control your Cellular, Wifi, or Bluetooth radio. In general, there should not be a need for this, because it is very dangerous - a rogue app can connect to a rogue network, which may be an attack vector, and in rare cases, radio may be used to track user location and movement! If unsure, turn all switches off.
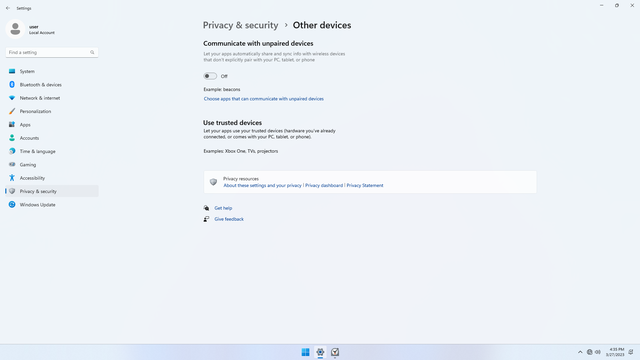
App permissions > Other devices
In Settings > Privacy & security > App permissions > Other devices, flip all switches off. This setting in particular may allow your device to communicate with a nearby stranger's device! Always keep this disabled unless absolutely necessary.
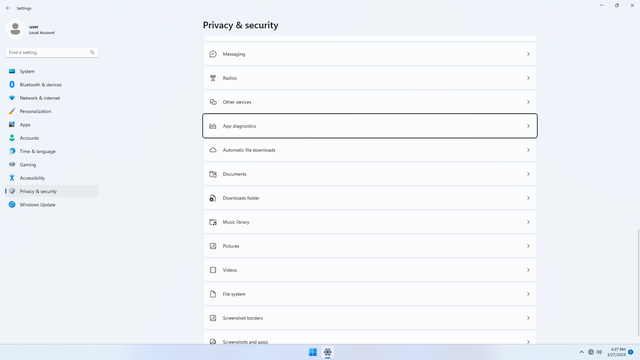
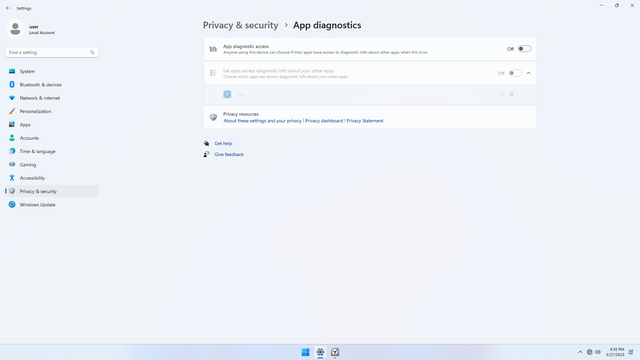
App permissions > App diagnostics
In Settings > Privacy & security > App permissions > App diagnostics, flip all switches off. This sends back app metrics to the developer (and possibly Microsoft), which might compromise personal data, regardless of whatever is claimed.
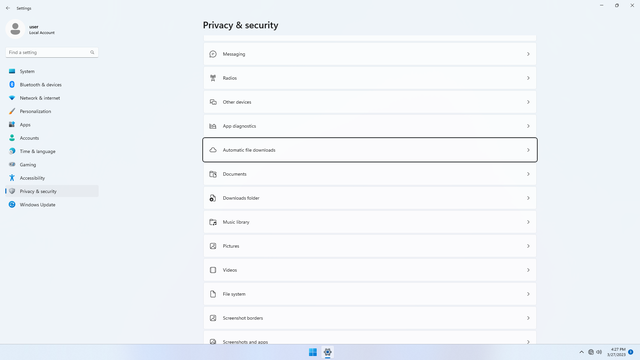
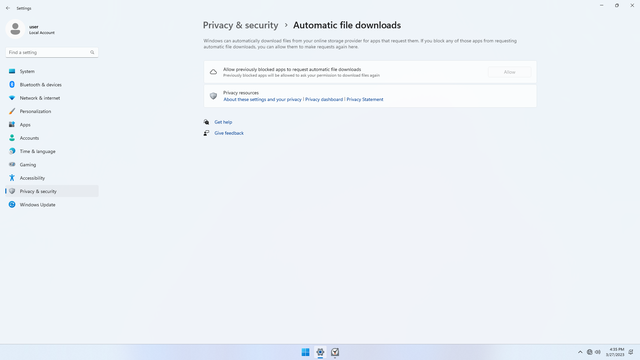
App permissions > Automatic file downloads
In Settings > Privacy & security > App permissions > Automatic file downloads, flip all switches off. This allows stuff like podcasts and certain apps to update themselves or their content in the background. If unneeded, flip this off.
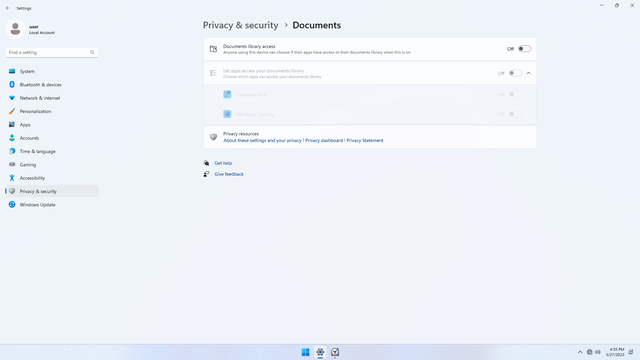
App permissions > Documents
In Settings > Privacy & security > App permissions > Documents, flip all switches off. Flip on only for apps you think needs access do your Documents folder. Sensitive documents falling into the wrong hands can be very costly.
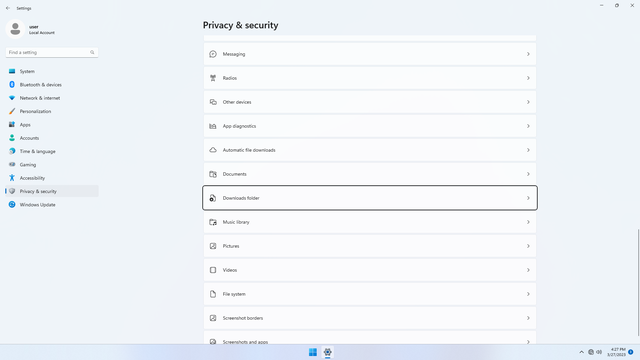
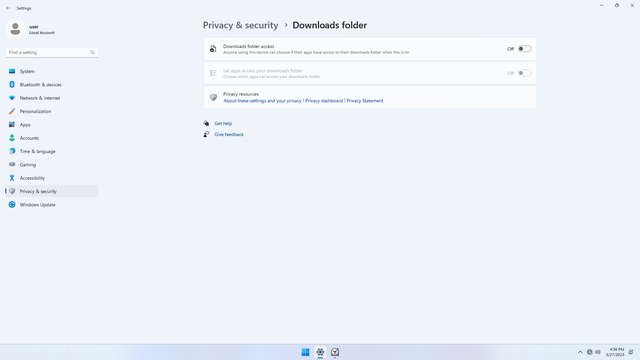
App permissions > Downloads folder
In Settings > Privacy & security > App permissions > Downloads folder, flip all switches off. Flip on only for apps you think needs access do your Documents folder. Malicious apps may mutate your existing downloads, such that if you execute a now malicious executable or file, it might cause your computer to get infected with a trojan. To be safest, keep this setting off.
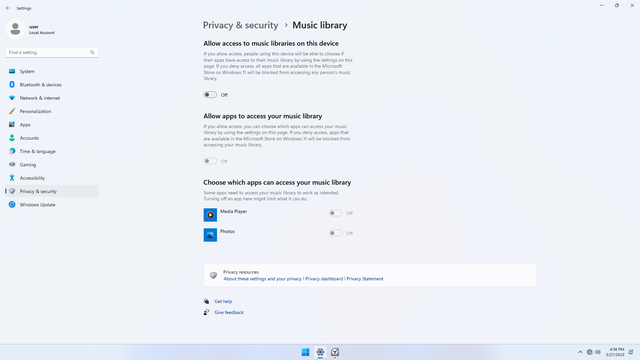
App permissions > Music library
In Settings > Privacy & security > App permissions > Music library, flip all switches off. Flip on only for apps you think needs access do your Music folder.
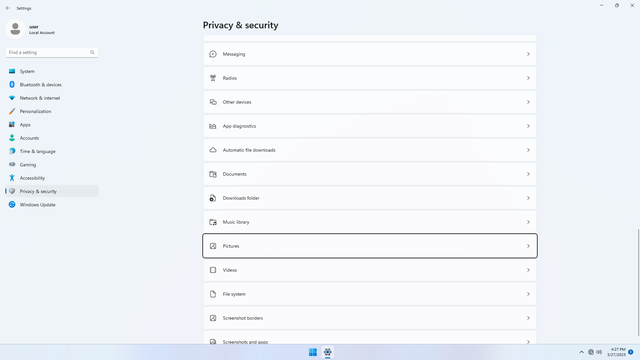
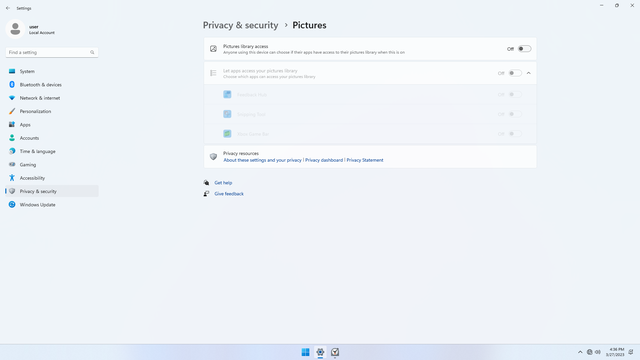
App permissions > Pictures
In Settings > Privacy & security > App permissions > Pictures, flip all switches off. Flip on only for apps you think needs access do your Pictures folder. Pictures may contain personal data, or may contain content of your contacts faces (friends, family). They also contain metadata such as location, date taken, and device information. Sensitive pictures falling into the wrong hands can be very costly.
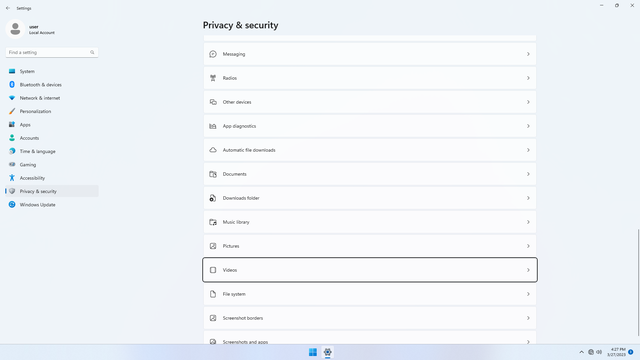
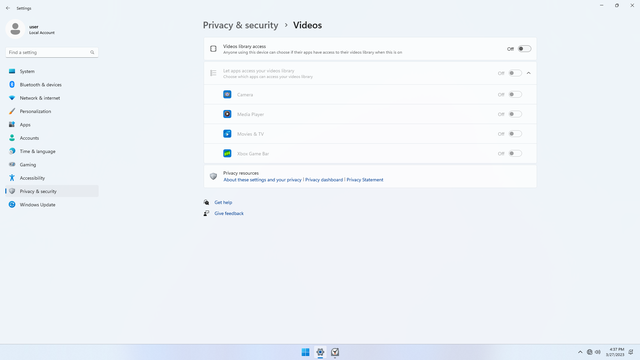
App permissions > Videos
In Settings > Privacy & security > App permissions > Videos, flip all switches off. Flip on only for apps you think needs access do your Videos folder. Videos may contain personal data, content of your contacts faces (friends, family), and audio data such as the voice data of people recorded. They also contain metadata such as location, date taken, and device information, and much more data than pictures. Sensitive videos falling into the wrong hands can be very costly.
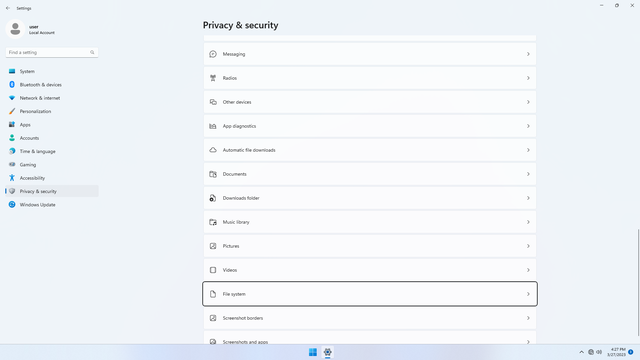
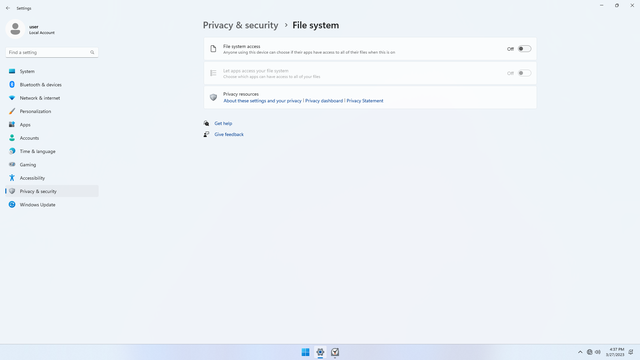
App permissions > File system
In Settings > Privacy & security > App permissions > File system, flip all switches off. This one is more dangerous than Downloads, becaues this permits apps to access the full filesystem, that means everything C:\ and all other drives. Always keep this switch off! If you need to transfer files from an app to C:\, first grant the app access to Documents, transfer files into Documents using the app, then in Windows copy files from Documents to whereever on the file system.
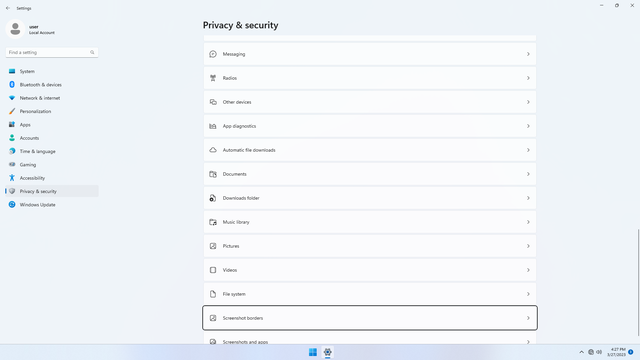
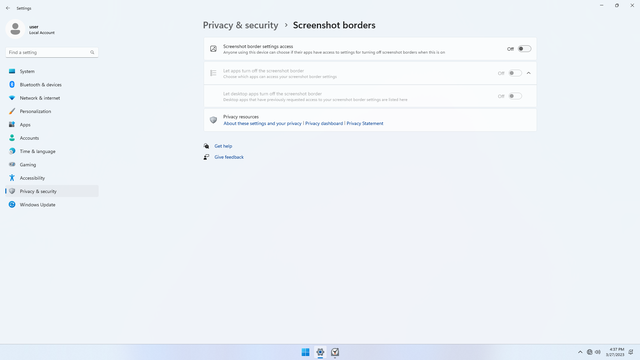
App permissions > Screenshot borders
In Settings > Privacy & security > App permissions > Screenshot borders, flip all switches off.
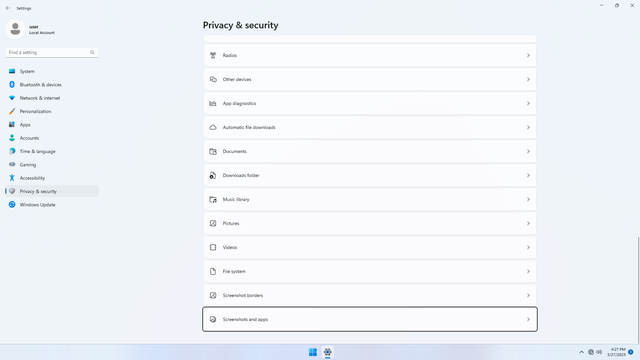
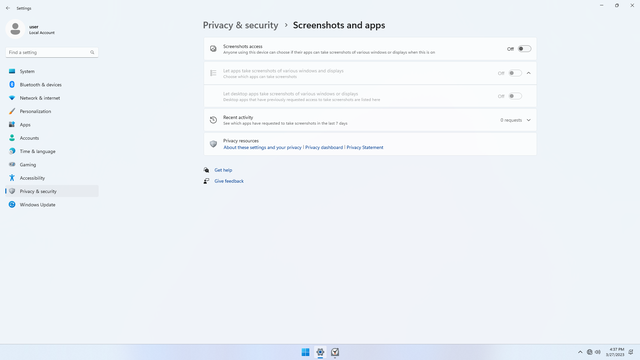
App permissions > Screenshots and apps
In Settings > Privacy & security > App permissions > Screenshots and apps, flip all switches off. Flip on only for apps you think you will use. Just like Pictures, screenshots may be used by malicious apps to spy on users and steal personal data.
Personalization
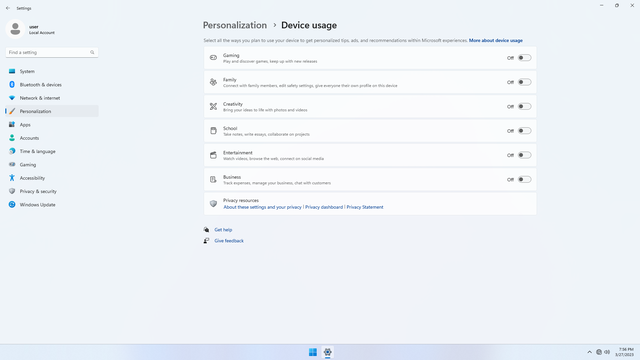
Device usage
In Settings > Personalization > Device usage, flip all switches off. This turns of all personalization for Microsoft services.
General guidelines for Privacy & security
- Opt out of targetted advertising where possible. There is no reason why a user's data should be sold by big tech and later used to influence the user
- Learning features (face recognition, speech, usage, typing) are background processes that constantly monitor user data (i.e. voice, usage patterns, typing patterns) because that's what they do for whatever they claim to do. If you do not feel comfortable with being constantly filmed, or being constantly listened to, or being constantly monitored about your app usage, or having your keystrokes being constantly monitored (think keyloggers), do not enable them. Remember that these learning features also compromise the privacy of other people within your device's vicinity. Disabling these features also significantly saves battery power, especially on phones.
- Disable sending diagnostic logs where possible. They can contain a lot of data and in rare occurrences, leak sensitive data about the device and user.
General guidelines for App permissions
- Always give room for possiblility of a device being hacked. That makes you uncomplacent in managing your personal data. Remember, as described above, your pictures, videos, camera, contacts, email, calendar, documents falling into the wrong hands all give away information of not just you, but your friends. Everybody ought to be responsible for their own data, and for everybody else's as well.
- Stick to the principle of least privilege. Always give apps only the permissions they ever only need. Do not use superpower apps for basic tasks, that require a bunch of permissions, when the same can be done using a basic app that requires only one privilege.
- Review app permissions from time to time, especially right after you install new apps. This gives you a good broad sense of what apps are using what permissions. That keeps your devices far less likely from getting compromised by some vulnerability.
- The above principles apply to any device you use.
Final thoughts
In today's tech world, a regular user's data is in danger of getting into the wrong hands, of not just big tech through data mining, but by attackers exploiting poorly managed (i.e. configured) access control policies on devices. Although there may already be fine-grained app and privacy controls in place in device Operating Systems (OSes), they are rarely effectively managed by users because of the tech world's lack of emphasis on their importance in protecting user data from those two particular groups. It is therefore critical for users to be well-informed on this topic.